Create your own code: from simple ciphers to complex algorithms
“When we are sure that we are fully protected, problems usually arise.”
Found on the internet
Who hasn’t wanted to experience the thrill of secrecy at least once? Inventing your own language, understood only by the chosen few? Surrounding yourself with an aura of mystery and occasionally chuckling at those who couldn’t decipher your secret notes.
Creating your own cipher is a fascinating activity that will help you understand the art and science of cryptography. And it will also help you discover the traits of both James Bond and Sherlock Holmes within yourself. To create your own cipher, you will need a bit of imagination, some creative thinking, and lots and lots of logic.
And, of course, at the very beginning, you should decide: what will bring you closer to creating your cipher faster – life solutions or technological ones?
Let’s begin inventing your own cipher. Personal interests can be of great help in this process. For example, if you are into the art of cooking, you can easily create your unique culinary cipher. The word “friend” for a secret message could be made from words like: “jam,” “ravioli,” “oysters,” “scallops.”
You can also include ciphers based on favorite drinks. C for English – Orange juice, H – A glass of wine, R – Lemon water. But if something goes wrong and you accidentally skip a letter while writing a secret message, then instead of “I love you,” the secret recipient will see “Orange juice, a glass of wine, lemon water.” This could easily lead to suspicions of an alcohol dependency.
The same works with animal codes. O – African elephant, M – Beaver, A – Camel.
Secret messages can be made melodic by replacing letters with natural sounds. The sound of rain could represent the letter A, the sound of an ATM could become the letter B, the noise of a party could replace the letter T, or O, or any other letter. For the recipient, the encrypted message would sound like a polyphonic etude. Though, you never know what could come back as a reply.
Movie ciphers will allow you to decrypt messages and recall the names of favorite movies or TV shows. Avatar will become the letter G, Batman will be letter R, and The Lord of the Rings will transform into the letter A. But that’s too easy. Why not use famous quotes from iconic films for the cipher?
The phrase “I’ll be back” can be encrypted with the opposite meaning.
The expression “Houston, we have a problem” can be read as “It’s five o’clock and I’m still trying to understand what this article is about.”
The phrase “my precious” from The Lord of the Rings could mean absolutely anything—it’s just a matter of figuring out what you consider “precious.”
Can there be a secret language within a language?
Yes, it is possible. You just need to create your own dictionary of code words and replace ordinary concepts with more vibrant and memorable ones. The word “meet” turns into “start the mission,” the phrase “print me ten” could mean “I expect exactly 24 pages of quality text for the presentation by dawn,” and “call me a foreman” will mean “call me a taxi.” Such a cipher adds necessary secrecy to your messages and might remind you of the existence of an outdated word dictionary.
For everyday ciphers, you can make words tumble around. So, “cutlet” becomes tclute, and the word “completely” turns into bsolteayu. The crazier the rearrangement, the more interesting it becomes. The key is not to overdo it, so even the most tired decryption expert can understand what hides behind the verbal acrobatics.
You can always turn the alphabet into a gallery of abstract art. Simply assign each letter—or even a group of letters—a unique symbol. It could be a mysterious sign, a geometric shape, or even just a squiggle. The letter P can become @, the letter H can turn into §, and the letter Y might become a bold upside-down heart ♥.
Any game can, if desired, be turned into a cipher.
Battleship is a game where you need to hit the enemy ship at the intersection of the cells. Well, isn’t that just a ciphering machine? But instead of ships, the game should have letters. For the conversation partner to read the message, they will need to send a key—coordinates must be specified.
A maze—a walking game—can help find the encrypted word, provided the correct path is chosen. By collecting scattered letters within the maze, the conversation partner will uncover the sought-after word or sentence.
For inventing your own cipher, molecular cuisine will also work. An encrypted message can be written using invisible ink. You can make an ink reservoir from bread crust, and milk can serve as the ink. A regular desk lamp will allow the recipient to read the message.
Lemon juice works on the same principle. Information written on a sheet of paper with lemon juice darkens when heated. A little ironing, and the secrets will be revealed. Beetroot juice, onion juice, apple juice, and other juices with high acidity also have the ability to change color when heated.
Candles can also become helpers in creating your own cryptography. The technique involves drawing lines on paper using wax, over which watercolor is placed. Where there is wax, the paint retreats, and the message written in wax emerges. This encryption method looks beautiful, as if the text is glowing from within.
And of course, the best cipher is one created for fun. Experiments, combining different techniques, and creating your own rules will confuse anyone. And then, secrets will be securely protected by self-made algorithms and positive emotions.
As with any creative process, it is important to test and improve your cipher. Write a few phrases and encrypt them. The best testers of your cipher will be your friends. They will definitely help you understand how effective and interesting your cipher is.

For those who enjoy technical solutions, there are always other options. Modern innovative possibilities can greatly simplify the process of creating a cipher and allow you to feel like a debutant cryptographer.
Sometimes the keys to the most secret data are not stored in safes, but in molecules. It sounds unusual, but a team of French scientists from the Sadrone Institute turned this idea into reality. They developed a molecular encryption key based on polymers.
Instead of sending encrypted messages over the internet, the initiative group decided to hide the molecular key in ink for regular writing and send it by mail. Recipients were to extract the key from the ink and decrypt the secret message.
The principle of molecular cipher operation is similar to a Lego set, where each brick (monomer) has its own unique shape and color. A peculiar “marker stone” indicates where the information is hidden in each polymer. The scientists created eight polymer chains, with each chain containing a coded part of the key. Then, they combined these polymers with isopropanol, glycerin, and soot, creating ink for writing letters.
The secret message can only be decrypted using liquid chromatography-mass spectrometry (LC-MS). It sounds intimidating, but it’s about analytical chemistry. The chemical process of decryption can be divided into several stages:
- The sample dissolves in a special liquid and passes through an adsorbent.
- Then the substance is separated into individual components.
- After that, these individual components reveal their true nature: mass and charge.
- That’s it. The masks are off—the molecules reveal their true face and structure.
And then the recipients with academic degrees received the coded information. They entered the molecular key and opened a regular text file with it, where the Wizard of Oz was hidden. This very work was delivered with high confidentiality. The development of molecular encryption keys could open up new, vast horizons in the field of information protection. And the first step has already been taken.
For those who absolutely want to invent their first cipher right in the digital world, the programming language Python comes to the rescue—philosophy dressed in code.
Moreover, Python can be used to write a convoluted cipher based on simple yet effective encryption methods. For instance, when writing an algorithm, you can use the Caesar cipher or the Vigenère cipher. To develop a basic user cipher, a simple letter shift in the alphabet will be enough.
For the uninitiated interceptor, the cipher will look like a random set of characters. “Кз хзгв хзгв” — such a message will be received by the recipient instead of the word “привет” and will remain completely puzzled unless they know the key’s patterns.
The encryption algorithm in Python looks like this:
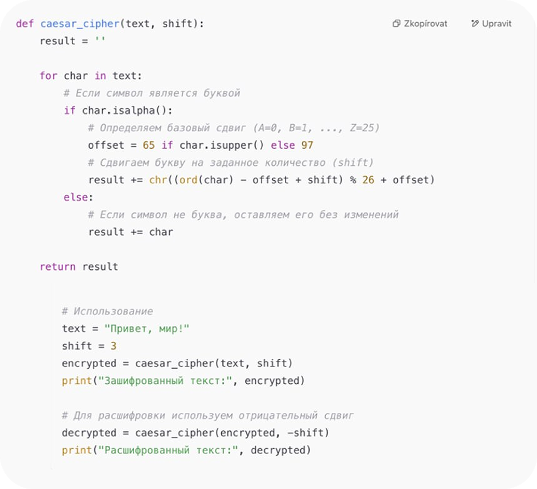
At first glance, nothing is clear. But the pattern and rules in the code are clearly visible.
ord(char): This function takes a character and returns its value from the ASCII table. Here, characters and symbols are assigned numeric values. For example, ord(‘A’) will return 65, as this is the ASCII code for the uppercase letter ‘A’.
chr(…):This function takes a number (ASCII code) and returns it as the corresponding character. For example, chr(65) will return ‘A’.
Shift: Shifting characters means moving each character a certain number of positions in the alphabet. For example, if we shift ‘A’ by 1 position, we get ‘B’.
Here’s another example of code that implements character shifting:
Let’s take the “tajnykluc” as the key, and the substitution table will look something like this:
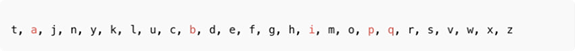
Although this is still not the final version. The given example can be modified: add support for uppercase letters and use more complex substitution rules (which can differ for each character). For this, you would need to generate a substitution table based on a different algorithm.

To generate the table, a key is required. For example, the same invented “tajnykluc,” which is cleared of duplicates. The key is added at the beginning, and the remaining letters of the alphabet follow it. For each character in the text, the corresponding symbol in the substitution table needs to be found.
For decryption, a decryption table is formed, which is obtained from the substitution table by sorting according to the substitute symbols.
The cipher looks like this:
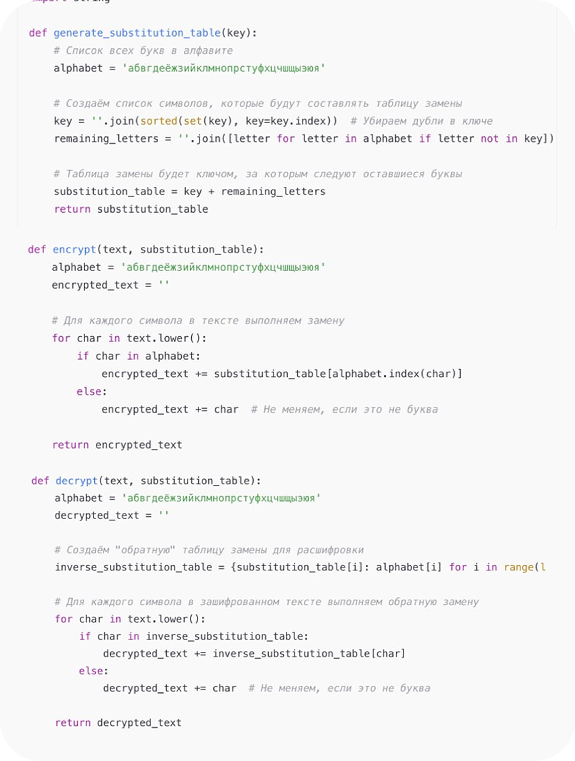
The accessibility of the method allows beginners to quickly master the basics and immerse themselves in the realm of algorithms and logic.
For those who are still learning the world of programming but still dream of creating their own cipher, there’s another technological solution—the SHA512 hash generator, a unique data keeper. It is designed to ensure the preservation and integrity of information in critical applications. This applies whether you are working in the field of web security, cryptographic protocols, or blockchain applications. The digital cipher helps you verify if your data is intact. It’s like a fingerprint—unique and irreplaceable. And the most interesting part—it’s impossible to retrieve the original information from the hash. Truly a unique data keeper.
You can create your own cipher using a hash generator on your own by following simple steps:
In the online generator, enter the text or data to be hashed in the special input field. After that, use the special button, and the tool will instantly generate the SHA512 hash for the input. Copy the hash and use the generated version to store passwords, verify files, or for cryptographic purposes. And then, no one prohibits you from combining this type of encryption with other methods, such as a symmetric block cipher algorithm—AES (Advanced Encryption Standard). After all, you’re the inventor, the choice is yours.
If the creative aspect is important to you when creating your own cipher, there’s also a technological solution for you—music. Music is eternal not only on the stage but also in encryption.
You can send someone an audio file with a national anthem or a song from the movie “Titanic,” in which the password is encrypted as an image. Some people knew but couldn’t do it, and some are hearing about it for the first time. In reality, it’s quite simple:
- Find or create an image that you want to encrypt (you can even do this without images and encrypt text). Write the message in any graphic editor and save the image in JPG format.
- Open the Coagula program. Using File → Open image, select the saved JPG image.
- In the menu, go to Sound → Render without blue, where the image is transformed into sound noise.
- Create an audio file and save it in WAV format using File → Save Sound as. The audio cipher is ready to be sent to anyone. The uninitiated will only hear strange sounds and noise.
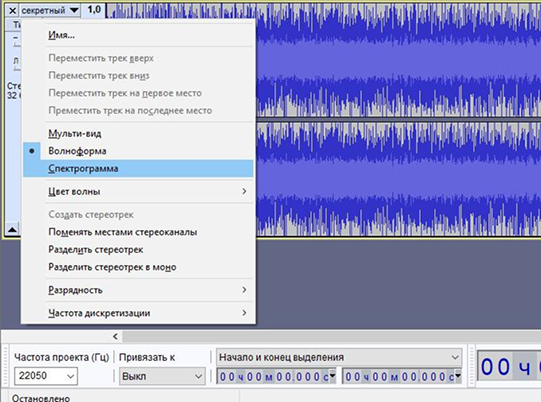
To revert the sounds back to a visual format, you will need a utility called Audacity. After installing it, open the audio file. Using the Shift + M keys, select the “Spectrogram” option.
And before your eyes will appear the encrypted password or the very secret you wanted to decode.
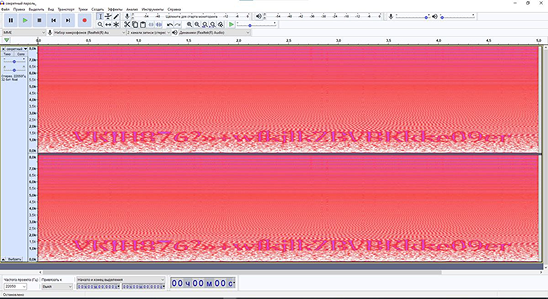
Creating your own cipher is both a challenging and rewarding process. By understanding the principles of cryptography and experimenting with various encryption techniques, you can develop a system—the very cipher that will meet all your needs and practical requirements. However, even the most reliable ciphers evolve, are tested, and improve over time, so the process of data encryption should still be left to the professionals.
In the meantime, you can try to decode the cipher we’ve hidden in this article. Good luck.
Linear-arithmetic synthesis is based on sound formation. We’ve synthesized the perfect formula of facts and interest.
Thank you!




